Risk Management
Basic Initiatives
We anticipate specific risks surrounding the entire Group from normal times and establish preventive measures against the losses caused by those risks. Furthermore, we take post-treatment measures and recurrence prevention measures to ensure the safety of employees’ lives and bodies and minimize losses even when risks become apparent.
Specifically, we create an environment in which preparations and measures necessary for business continuity and stable development can be taken effectively and efficiently by formulating Risk Management Policy and clarifying the definition of risk, management system, information management policy, etc. in Stanley.
In addition, we implement company-wide risk management such as risk analysis/identification and preparation of a risk aversion manual with the Risk Management Committee chaired by a Director playing a key role. Risk Management Committee is held regularly irrespective of whether or not an incident has occurred, and promotes the formulation and approval of “key risks” and “risk scenarios,” and communications of them to divisions and supervising departments. If a risk were to materialize, the Risk Management Committee would set up a BCP (Business Continuity Plan) Headquarters to take an integrated response to the occurrence of an incident.
We are currently reviewing our risk management system to ensure we are able to respond in a flexible and agile manner to various newly foreseen risks.
Review of the Risk Management System
To respond flexibly and in an agile manner to various newly foreseen risks, we have reviewed and reorganized our risk management system. Having added representatives from the production, sales, and technical departments to the members of the Risk Management Committee that conducts comprehensive risk management—by, for example, risk analysis/ identification and the preparation of a risk aversion manual—we have put in place a system to respond to a wide variety of risks. Risk Management Committee meetings are held regularly irrespective of whether an incident has occurred. If a risk were to materialize, the Risk Management Committee would set up a Business Continuity Plan (BCP) Headquarters to take an integrated response to the occurrence of an incident.
Risk Management Committee System
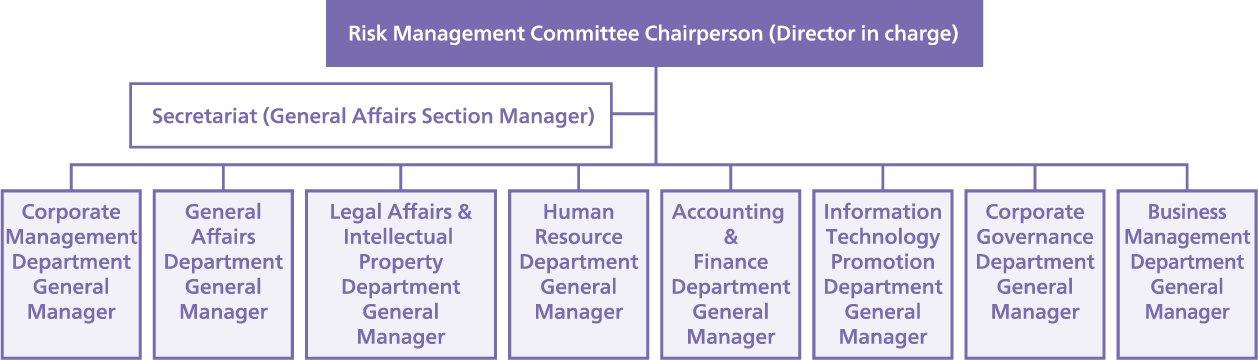
The Risk Management Committee anticipates specific risks surrounding the entire Group and establishes measures to prevent losses caused by such risks, as well as ensures safety in the event of crises and minimizes losses by taking measures in an effective and efficient manner to deal with the aftermath and prevents such events from recurring, to ensure continuity and stable growth of businesses.
Examples of Potential Risks
Key Risks
- Crisis management system
- Business continuity risk
- Sustainability management
- Human capital risk
- Quality risk
Major Anticipated Risks
- Natural disasters (e.g., earthquakes, typhoons)
- Fire, explosion, and other unexpected incidents
- Environmental pollution
- Violation of laws and regulations (e.g., violation of Antimonopoly Act, product regulations)
- Product liability
- Cyberattacks/information leaks/data breaches
- Spread of infectious disease
- Human resources and labor issues
- On-the-job accidents
- Bankruptcy of suppliers
Specific Risks Surrounding the Company
In recent years, natural disasters due to climate change caused by global warming have become more frequent in many areas. There are inherent risks, such as insufficient supply of raw materials and parts from suppliers and a decrease in customer production capacity, that may have a negative impact on our performance and financial conditions. In preparation for the possibility of such risks becoming apparent, we are working to minimize the impact by taking necessary measures for business continuity, such as a preliminary examination of the installation of disaster prevention equipment and production transfer implementation of disaster drills/BCP training, and others.
We also consider the risks posed by climate change using the analytical processes of the Risk Management Committee and monitor them regularly.
Information Security
Considering information security to be one of our important business challenges, we have in place the Information Security Basic Policy to protect personal information and other confidential information, and implement appropriate information security measures to ensure secure management.
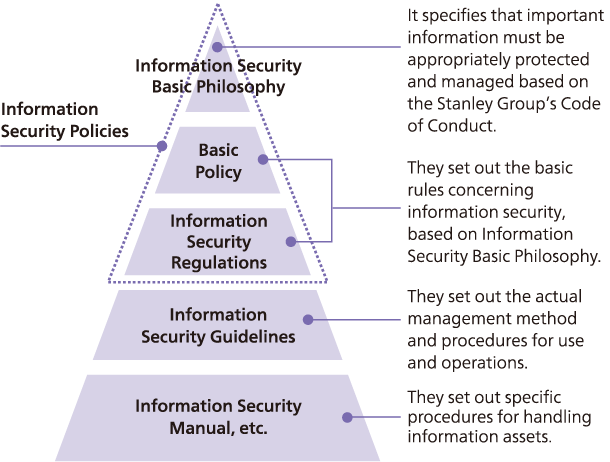
Information Security Basic Policy
Stanley Group appropriately protects and manages important information based on the Stanley Group’s Code of Conduct. In doing so, we set activity targets with the goal of achieving the appropriate level of information security and work to improve the Stanley Group’s level of information security. Our Information Security Basic Policy is set out below.
- 1
Scope of application
The information security management system (the “ISMS”) applies to all information assets related to our business activities.
This policy applies to all of those who handle information assets owned by our employees, etc. - 2
Handling of information assets
Information assets refer to information and machines and structures that process information (including information systems and materials for system development, operation, maintenance and information services provided by service providers). They shall be maintained and managed in a well-balanced manner from the three perspectives of confidentiality, integrity and availability, and be effectively utilized. - 3
Establishment, maintenance and improvement of the ISMS
In order to establish and continuously maintain the ISMS, we shall establish relevant organizations and systems and carry out regular reviews, thereby ensuring continual improvement. - 4
Implementation of information security measures
We shall identify and quantify the threat and the vulnerability against the confidentiality, integrity and availability of information assets.
Thereafter, we shall carry out regular risk assessments, and evaluate and continuously review our risk treatment. - 5
Compliance with applicable laws and regulations
Our employees shall comply with laws, regulations, social norms, contracts and internal regulations applicable in respect of handling information assets. - 6
Education about information security
We shall provide education and awareness necessary to ensure that the Information Security Basic Policy is complied with and information security measures are thoroughly implemented. - 7
Incident prevention and response
We work to prevent an information security incident from occurring, and in the event of the occurrence of an incident, we shall investigate the cause and promptly implement response measures. In addition, in the event of any breach of the information security, we will impose a severe punishment pursuant to applicable internal regulations and shall take appropriate measures to prevent a recurrence.
Framework for Implementing Information Security Activities
At Stanley Electric, overall information security activities are controlled by the Information Security Secretariat established within the information systems department. General Managers of departments assume a role of Management Representative for information security, and implement information security activities of their own department together with information security personnel, network administrators and system administrators they appoint.
At the Group’s affiliates, they have the Information Security Secretariat in place, with their Presidents as Supervising Representatives for information security. As is in the case of Stanley Electric, General Managers of their departments assume a role of Management Representative for information security, and implement information security activities of their own department together with information security personnel, network administrators and system administrators they appoint.
Information Security System
Security Countermeasures on a Global Scale
Having put in place a communication infrastructure that ensures security for the entire Group, we acquired certification for two of our domestic and two overseas offices under the industry standard for ensuring cybersecurity (TISAX) developed in Europe. By the end of FY2025, we plan to implement global security measures in the fields of IT and OT, including the development of infrastructure that effectively utilizes technology.
